The good and the bad
After spending six months in the Information Systems Security service of the Société Générale, I have got really impressed by how the security was managed!
To be clear, doing security on my free time gave me a pessimist opinion on
security when managed by big companies.
But working with such a service as the ISS one from the SG changed my mind. In
my humble opinion, they are doing excellent job!
Take it as you want of course, I am just a student with no real experience :/
But today I stumbled into such a bad password policy that it blew my mind, in a bad way (sigh).
The password policy from my ISP
Today I had to connect on my ISP (Internet Service Provider) website, in order
to fill a paper about the new SEPA norm.
TL;DR: the SEPA - Single Euro Payments Area - is a new norm that aims to
provide an unique way to do online payments for the European union (huge
project here!)
Since it was the first time I went on their website, my ISP asked me to provide a password that will protect my account and there is the form:
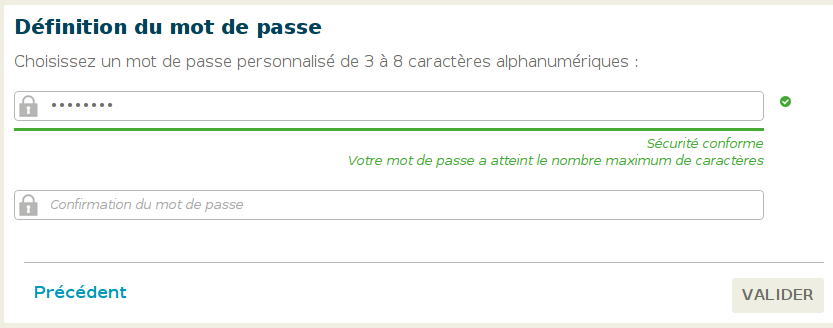
For those who do not speak French, the form translates as the following:
Definition of your password
Choose your private password from 3 to 8 alphanumeric characters
(in green) Conformed security
(in green) Your password fulfills the maximum characters allowed.
3 to 8 characters? Alphanumeric?

By the way, the password I wrote in the form was qwertyui.
Hopefully, this password is conform to their security policy! I feel secure
now!
What is even funnier? Their full policy.

Translation:
Your password has to follow the rules below:
- from 3 to 8 characters among "a-z", "0-9" and "_"
- only lowercase characters
- no whitespace nor accent
- the "_" cannot be in the first position
No only the characters have to be alphanumeric but they have to be lowercase!

What about the "_" not in the first position? Do not tell me that they don't know how to manage a database! Is it like 'id_password'? With some luck it is even saved in clear into their table...
FYI, here is a table that describes how long it might take to bruteforce a password according to its policy:

Few thoughts
I am scared by their policy. They are not just the website of my local association, they are my ISP!
On their website, my personal information appears (my first name, last name, my address, my email address and my phone number for instance). I can also change my offer to something more expansive and check my bills.
So if one day, my ISP provider gets hacked and their database gets leaked (and referenced here for instance), I will not be surprised to see their user passwords cracked in less than one week...

Funny thing, I still didn't fill that paper...