SecuRT third edition took place last Saturday in Montbéliard. It is a special event that tries to raise awareness about security in computer sciences among students. During the first edition, I participated to their CTF, with jvoisin and rboissat under the name of HackGyver, where we finished first!

Since last year, we decided to organize the challenges for their competition and last week-end, we provided more than 40 different challenges. Now that the event is over, I wanted to review some details here.
I will only speak about the part futex, jvoisin and I contributed to. The fact that the communication about the event was incomplete, that the website is ugly or that the new name is lame will not be covered.
The Bad
Unsecure Setup
I want to thanks the participants! Because they were nice enough to not break the setup.
We had set up three different virtual machines for the CTF. One for the exploits, one for the web challenges and one for the scoreboard. It could have been enough for such small competition except that we had some web challenges that were hazardous.
- One was a path traversal vulnerability. The objective was to read
config.phpin the web directory using php filter. - Another one was to upload a PHP backdoor via a MIME-type attack.
In both cases, the students could have read the flags from the other web challenges without even reading the
subjects.
We knew that. We did not do anything against that. We sucked.
Next year, we will configure one VM for each hazardous challenge (we will need better hardware though) for better isolation.
Broken challenges
More than 40 different challenges were provided for the CTF. Truth be told, most of them were written in the past two weeks.
We spent some times to test each of them and we noted a couple of things to update right before starting for the CTF. Of course we forgot some of them...
- With the MIME-type challenge, the challenger should have recovered the source code (available in
/robots.txt) in order to know how the files were renamed (md5(date('Y-m-d H:i') . $filename)). But we forgot to forbid the directory listing in the upload directory. The challenger only had to get the list and access his backdoor. - For the exploit challenges, we decided to make them easier by adding an unused function that would read the
flag.txtfile for them. Hence, in order to exploit the binary, you only had to override theEIPwith the offset of that function. - In one of the challenges, we called the unused function in the main just to be sure that everything was working fine. And of course, we forgot to remove it... Therefore the exploit was run the binary, read the flag SO hard!
Another aspect that bothered me is that some challenges could be solved using automated tools only. Script kiddies would have been able to solve some challenges like the SQLi using sqlmap, the Format String one thanks to RedSpin and others... But we thought that because the participants are mostly beginners, it would not be a problem. IMO next year, we should think about that and make it hard for these tools to work.
Gap between challengers
There was 8 teams that participated to the CTF and most of them never did anything related to security. I tried my best to help the beginners, giving them advices, showing them some tools, being their rubber duck and some times spoiling a little bit too much :p
I was glad that most of the Web and SQLi challenges were validated but still surprised that the Reverse Engineering category was not even checked...
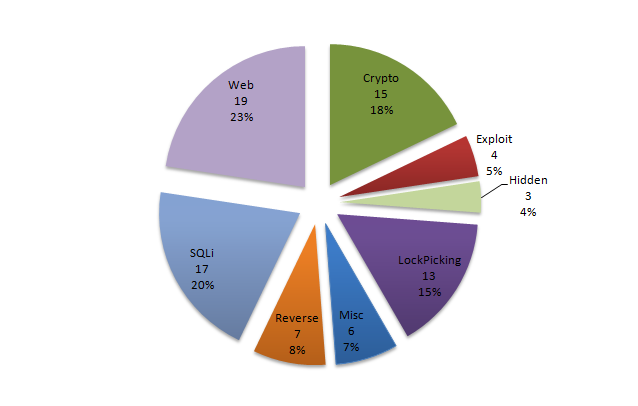
The RE category had the most challenges and some were really simple. I know that the participants most probably never tried some reverse stuff but come on...
- The first challenge was the most obvious one that we could have prepared for beginners run strings and validate. Only 3 teams validated it...
- The second challenge I think was easy is the Android APK. There was no real difficulty run dex2jar, use jd-gui,
rot13 the flag. Plus, it's not like reversing a
rot13in ASM, this is Java meaning that it is easy to read. - In the misc category, the Telnet pcap challenge was validated only 4 times...
Lame challenges
Last point I want to cover is that some challenges were lame... With more that 40 challenges, it is hard to have each of them being fun and interesting.
- A web challenge consisted in bypassing a broken authentication system that was using
==instead of===when comparing the passwords. A couple of days before the event, we decided to reduce the points for the challenge and to give the source code but we forgot the last one. It made the challenge a pure guess and die not really fun. - A misc pcap challenge I thought would be funny was actually pretty lame because of one detail. When creating a misc challenge, avoid using junks. I thought that without the junk network exchanges, the challenge would have been too obvious but in that was a bad idea. Instead, it made it super annoying and nobody focused on it at all...
- The crypto challenges were sooooo lame... But in our defense, none of us (except jvoisin that was busy with the Boston Key Party) are lame with crypto stuff. We still wanted to provide some challenges but they were not really interesting, IMO.
The Good
Most challenges were validated
To be precise, we provided 44 challenges for this third SecuRT edition. Among them, 32 challenges were validated at least once, which makes it ~73%!
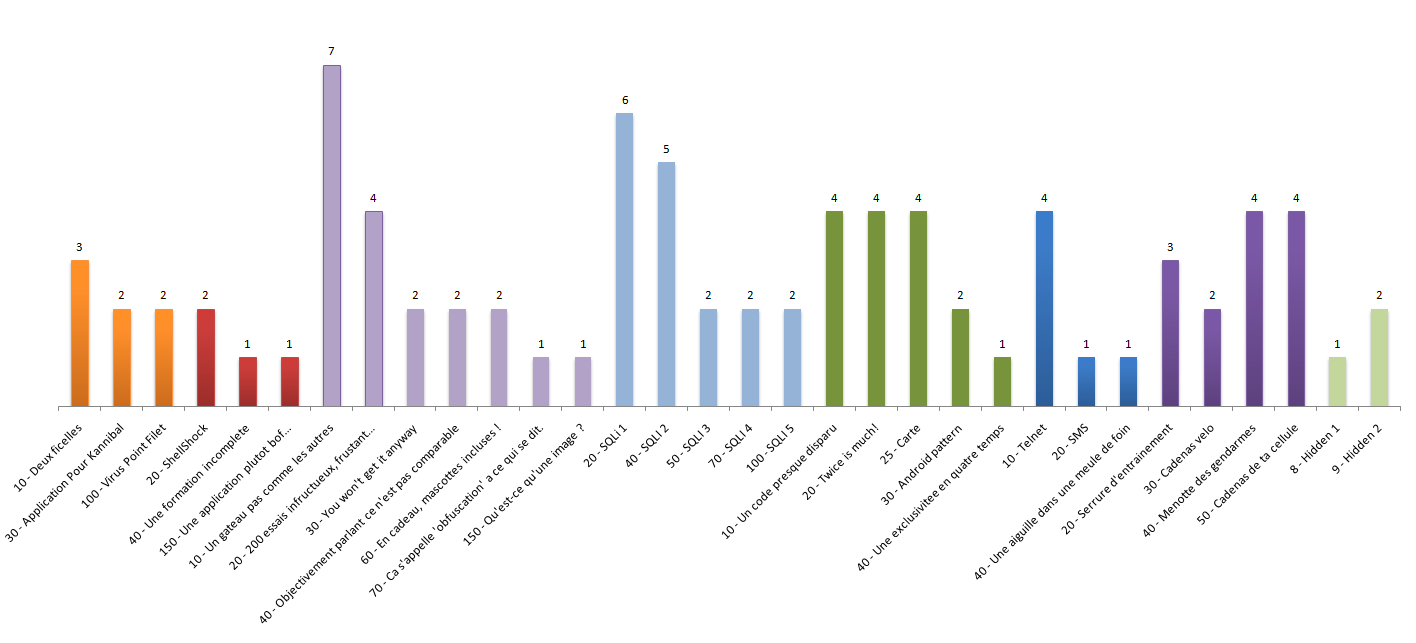
As explained earlier, most of the validated challenges were the web and the SQLi ones. Being come the crypto and the lock-picking ones. As seen last year, the lock-picking ones were really appreciated by the challengers; it is always fun to have the opportunity to unlock some real locks :)
Good duration
A few days before the event, we asked to have 7 hours allocated for the CTF instead of 4. With 40 challenges, we really thought that 4 hours would not be enough and we were right. First we asked for 12 hours but we were afraid to lose the challengers' focus before the end and we were right again.
IMO 7 hours was almost perfect. On the dark side, we saw a lot of people leaving early but I think that was because we should have extended the duration way earlier. People already had plans for the evening. On the bright side, most of the challenges were validated and the ones who stayed said that they had fun.
I hope that next year, we will do what has been said during event, meaning two days for the SecuRT:
- Fist day for the conferences, the open forums, the workshop, etc.
- Second day for the CTF. 12 hours or 24 hours with the corresponding logistic behind (beds, food, transports).
I am waiting to see what can be done!
People had fun
Walking around during and after the CTF, I feel that the challengers had fun. I realized that most of them had a hard time just to validate the first web challenge but with some little help, they felt like pwning some stuff :p
I am quite sure that we indeed raised awareness among them, especially with some challenges seen in the wild not so long ago. In my opinion, the SecuRT CTF went fine.
Scoreboard
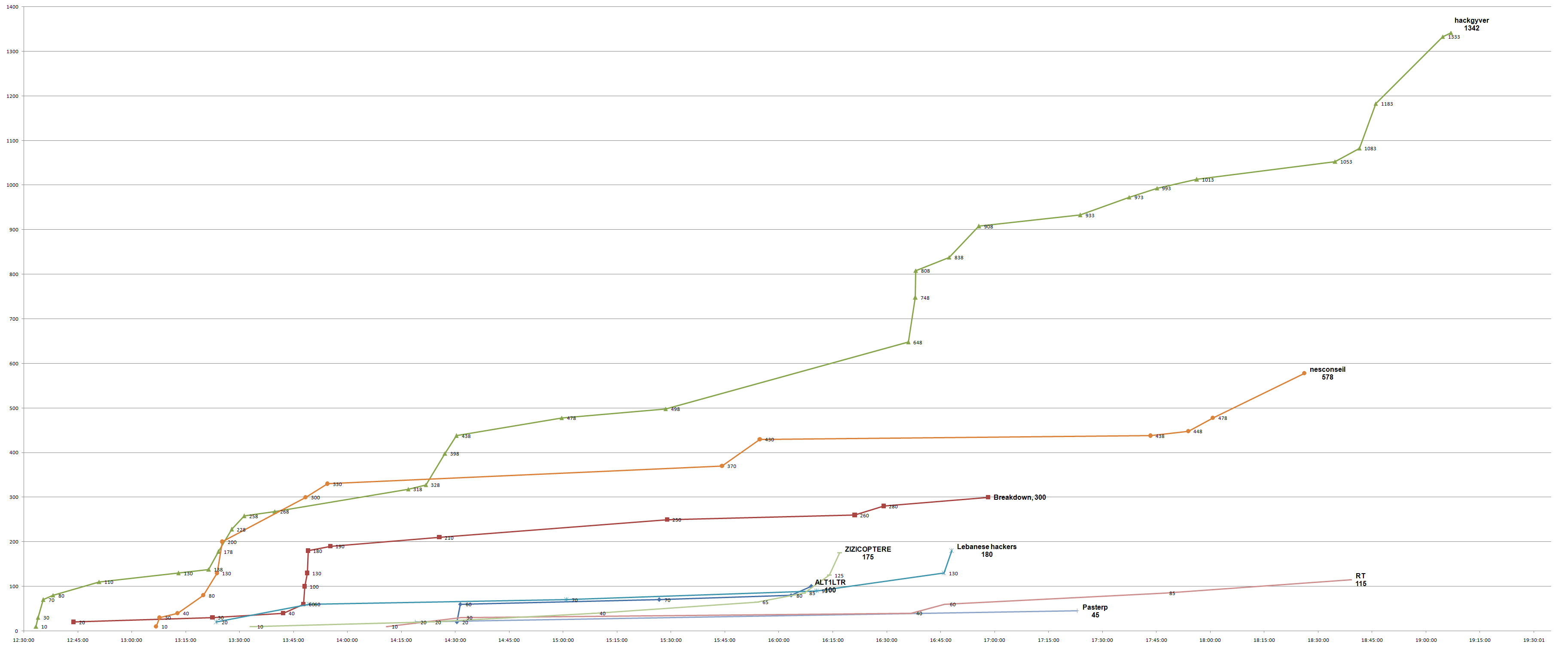
- The two members of HackGyver, kiwhacks and xarkes (not part of the organisation so no cheats here) arrived first so good job to them!
- A huge GG for the only member of the team RT to have stayed until the end of the CTF! He was a real beginner but never gave up! He is the real winner of the CTF here :)
Thanks to all participants! We hope to see you next year for even better challenges! Feel free to stop by the hackerspace :p